
𝐓𝐨𝐩 𝟏𝟎 𝐂𝐲𝐛𝐞𝐫𝐬𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐓𝐡𝐫𝐞𝐚𝐭𝐬 𝐢𝐧 𝟐𝟎𝟐𝟓 𝐚𝐧𝐝 𝐇𝐨𝐰 𝐭𝐨 𝐌𝐢𝐭𝐢𝐠𝐚𝐭𝐞 𝐓𝐡𝐞𝐦?
Jun 04th, 2025
As we move deeper into 2025, cyber threats are becoming more intelligent, automated, and harder to detect. From AI-generated deepfakes to the threat of quantum computing, today’s digital dangers demand smarter defenses. Whether you’re a business owner, IT professional, or security enthusiast, staying ahead of these threats is no longer optional—it’s essential. Here’s your guide to the top cybersecurity threats in 2025 and how to defend against them.

𝟏. 𝐀𝐈-𝐏𝐨𝐰𝐞𝐫𝐞𝐝 𝐂𝐲𝐛𝐞𝐫𝐚𝐭𝐭𝐚𝐜𝐤𝐬: 𝐓𝐡𝐞 𝐃𝐨𝐮𝐛𝐥𝐞-𝐄𝐝𝐠𝐞𝐝 𝐒𝐰𝐨𝐫𝐝
AI is revolutionizing both offense and defense in cybersecurity. Hackers now use AI to create intelligent malware and hyper-personalized phishing schemes.

𝐇𝐨𝐰 𝐭𝐨 𝐌𝐢𝐭𝐢𝐠𝐚𝐭𝐞:
1.Implement AI-driven security systems.
2.Train staff to spot AI-manipulated scams.
3.Partner with AI researchers to anticipate threats.
𝟐. 𝐃𝐞𝐞𝐩𝐟𝐚𝐤𝐞 𝐒𝐜𝐚𝐦𝐬: 𝐓𝐡𝐞 𝐑𝐢𝐬𝐞 𝐨𝐟 𝐒𝐲𝐧𝐭𝐡𝐞𝐭𝐢𝐜 𝐃𝐞𝐜𝐞𝐩𝐭𝐢𝐨𝐧
Deepfakes are no longer experimental—they’re a real threat. They can be used to impersonate executives or create fake video calls that trick employees into sharing data or sending money.

𝐇𝐨𝐰 𝐭𝐨 𝐌𝐢𝐭𝐢𝐠𝐚𝐭𝐞:
1.Use video authentication tools.
2.Confirm sensitive requests through multiple channels.
3.Raise awareness about deepfake tactics.
𝟑. 𝐐𝐮𝐚𝐧𝐭𝐮𝐦 𝐂𝐨𝐦𝐩𝐮𝐭𝐢𝐧𝐠 𝐓𝐡𝐫𝐞𝐚𝐭𝐬: 𝐁𝐫𝐞𝐚𝐤𝐢𝐧𝐠 𝐄𝐧𝐜𝐫𝐲𝐩𝐭𝐢𝐨𝐧 𝐍𝐨𝐫𝐦𝐬
Quantum computing may still be emerging, but it poses a serious risk to traditional encryption methods, making long-term data vulnerable.

𝐇𝐨𝐰 𝐭𝐨 𝐌𝐢𝐭𝐢𝐠𝐚𝐭𝐞:
Begin migrating to quantum-safe encryption.
Review existing data protection protocols.
Stay informed on cryptographic developments.
𝟒. 𝐑𝐚𝐧𝐬𝐨𝐦𝐰𝐚𝐫𝐞-𝐚𝐬-𝐚-𝐒𝐞𝐫𝐯𝐢𝐜𝐞 (𝐑𝐚𝐚𝐒): 𝐂𝐫𝐢𝐦𝐞 𝐟𝐨𝐫 𝐇𝐢𝐫𝐞
Ransomware kits are now being sold on the dark web, allowing anyone to launch attacks. The result? A surge in ransomware incidents.

𝐇𝐨𝐰 𝐭𝐨 𝐌𝐢𝐭𝐢𝐠𝐚𝐭𝐞:
1.Maintain regular offline backups.
2.Segment your networks.
3.Train employees to avoid phishing and suspicious links.
𝟓. 𝐈𝐨𝐓 𝐕𝐮𝐥𝐧𝐞𝐫𝐚𝐛𝐢𝐥𝐢𝐭𝐢𝐞𝐬: 𝐔𝐧𝐩𝐫𝐨𝐭𝐞𝐜𝐭𝐞𝐝 𝐃𝐞𝐯𝐢𝐜𝐞𝐬 𝐄𝐯𝐞𝐫𝐲𝐰𝐡𝐞𝐫𝐞
Smart devices—from thermostats to factory equipment—can be exploited as entry points into networks if not secured properly.

𝐇𝐨𝐰 𝐭𝐨 𝐌𝐢𝐭𝐢𝐠𝐚𝐭𝐞:
1.Change default settings and passwords.
2.Keep firmware updated.
3.Monitor traffic from IoT devices.
- 𝐒𝐮𝐩𝐩𝐥𝐲 𝐂𝐡𝐚𝐢𝐧 𝐀𝐭𝐭𝐚𝐜𝐤𝐬: 𝐈𝐧𝐝𝐢𝐫𝐞𝐜𝐭 𝐄𝐧𝐭𝐫𝐲 𝐏𝐨𝐢𝐧𝐭𝐬
Attackers are no longer targeting companies directly—they’re breaching suppliers and vendors to access bigger targets.
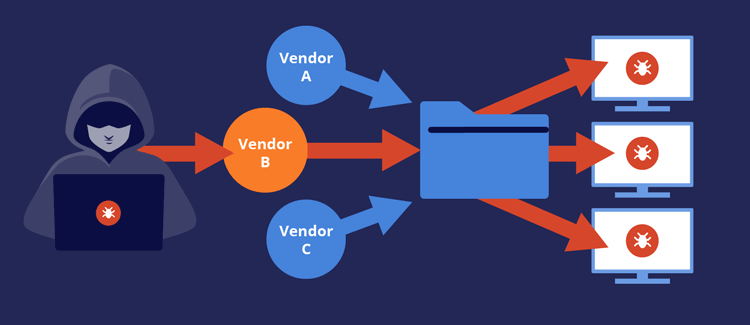
𝐇𝐨𝐰 𝐭𝐨 𝐌𝐢𝐭𝐢𝐠𝐚𝐭𝐞:
1.Audit third-party vendors regularly.
2.Use zero-trust architecture for external integrations.
3.Restrict access permissions by role.
𝟕. 𝐂𝐥𝐨𝐮𝐝 𝐒𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐌𝐢𝐬𝐜𝐨𝐧𝐟𝐢𝐠𝐮𝐫𝐚𝐭𝐢𝐨𝐧𝐬: 𝐓𝐡𝐞 𝐈𝐧𝐯𝐢𝐬𝐢𝐛𝐥𝐞 𝐑𝐢𝐬𝐤
Incorrect cloud settings have become a leading cause of data leaks. It’s not the cloud that’s unsafe—it’s how you configure it.

𝐇𝐨𝐰 𝐭𝐨 𝐌𝐢𝐭𝐢𝐠𝐚𝐭𝐞:
1.Use automated cloud security tools.
2.Regularly audit configurations.
3.Educate teams about cloud security best practices.
𝟖. 𝐈𝐧𝐬𝐢𝐝𝐞𝐫 𝐓𝐡𝐫𝐞𝐚𝐭𝐬: 𝐃𝐚𝐧𝐠𝐞𝐫 𝐟𝐫𝐨𝐦 𝐖𝐢𝐭𝐡𝐢𝐧
Employees or contractors—intentionally or not—can leak, steal, or destroy sensitive data, making insider threats an ongoing risk.

𝐇𝐨𝐰 𝐭𝐨 𝐌𝐢𝐭𝐢𝐠𝐚𝐭𝐞:
1.Monitor internal activities with behavioral analytics.
2.Enforce access control and segmentation.
3.Foster a culture of security responsibility.
𝟗. 𝐀𝐈 𝐢𝐧 𝐂𝐲𝐛𝐞𝐫 𝐃𝐞𝐟𝐞𝐧𝐬𝐞: 𝐒𝐦𝐚𝐫𝐭𝐞𝐫, 𝐅𝐚𝐬𝐭𝐞𝐫 𝐑𝐞𝐬𝐩𝐨𝐧𝐬𝐞
Just as AI can attack, it can defend. AI helps detect threats faster, analyze behaviors, and automate responses—cutting response times drastically.

𝐇𝐨𝐰 𝐭𝐨 𝐌𝐢𝐭𝐢𝐠𝐚𝐭𝐞:
1.Integrate AI-based detection tools.
2.Continuously train models with new threat data.
3.Combine AI with expert oversight.
𝟏𝟎. 𝐑𝐞𝐠𝐮𝐥𝐚𝐭𝐨𝐫𝐲 𝐏𝐫𝐞𝐬𝐬𝐮𝐫𝐞: 𝐂𝐨𝐦𝐩𝐥𝐢𝐚𝐧𝐜𝐞 𝐚𝐭 𝐭𝐡𝐞 𝐂𝐨𝐫𝐞
Regulations are evolving. Compliance is not just about avoiding fines—it’s about building trust and accountability in the digital age.

𝐇𝐨𝐰 𝐭𝐨 𝐌𝐢𝐭𝐢𝐠𝐚𝐭𝐞:
1.Assign a dedicated compliance lead.
2.Stay current on global and industry-specific regulations.
3.Use tools for automated policy enforcement and audit trails.
✅𝐓𝐚𝐤𝐞 𝐀𝐜𝐭𝐢𝐨𝐧 𝐍𝐨𝐰: 𝐏𝐫𝐨𝐭𝐞𝐜𝐭 𝐖𝐡𝐚𝐭 𝐌𝐚𝐭𝐭𝐞𝐫𝐬
Cybersecurity isn’t just an IT issue—it’s a business priority. Don’t wait until you’re the next headline. Whether you need a cybersecurity audit, employee training, or enterprise-grade protection, we’re here to help.
📧 Email: admin@incognitai.com
📞 Call: +91 99522 89956
𝐘𝐨𝐮𝐫 𝐝𝐞𝐟𝐞𝐧𝐬𝐞 𝐬𝐭𝐚𝐫𝐭𝐬 𝐧𝐨𝐰. 𝐋𝐞𝐭’𝐬 𝐦𝐚𝐤𝐞 𝐲𝐨𝐮𝐫 𝐝𝐢𝐠𝐢𝐭𝐚𝐥 𝐰𝐨𝐫𝐥𝐝 𝐦𝐨𝐫𝐞 𝐬𝐞𝐜𝐮𝐫𝐞!