
10 Must-Have Tools for Cross-Platform Mobile App Development in 2025
Jun 21st, 2025
In 2025, cross-platform mobile development continues to evolve, empowering developers to build high-performance apps for iOS, Android, web, and desktop—all from a single codebase. Whether you’re a startup in Coimbatore or a global enterprise, choosing the right tools is crucial for success. This guide explores the top 10 cross-platform development tools, analyzes the ongoing Flutter vs. React Native debate, and highlights emerging mobile SEO trends.

🚀 Top 10 Cross-Platform Mobile App Development Tools in 2025
1. Flutter (Google)

- Overview: Flutter remains a leading choice for developers seeking high-performance, visually rich applications.
- Key Features:
- Utilizes the Impeller rendering engine, replacing Skia, for smoother animations and reduced jank.
- Ahead-of-Time (AOT) compilation ensures faster startup times.
- Supports web and desktop platforms, enhancing its versatility.
- Ideal For: Projects requiring custom UIs and consistent performance across platforms.
2. React Native (Meta)

- Overview: Backed by Meta, React Native continues to be a robust framework for building native-like apps using JavaScript and TypeScript.
- Key Features:
- Introduces a new architecture with Fabric and TurboModules for improved performance.
- Hermes engine reduces memory usage and enhances startup times.
- Strong community support with a vast ecosystem of libraries and tools.
- Ideal For: Teams with JavaScript expertise aiming for rapid development cycles.
3. Ionic
- Overview: Ionic is an open-source framework that enables developers to build hybrid mobile, web, and desktop applications using web technologies.
- Key Features:
- Provides a library of pre-designed UI components.
- Integrates with Angular, React, and Vue.js.
- Utilizes Capacitor for native functionality.
- Ideal For: Web developers looking to transition into mobile app development.
4. .NET MAUI (Microsoft)
- Overview: The evolution of Xamarin.Forms, .NET MAUI allows developers to create cross-platform apps using C# and .NET.
- Key Features:
- Supports Android, iOS, macOS, and Windows.
- Single project structure simplifies development.
- Deep integration with Visual Studio enhances productivity.
- Ideal For: Enterprises invested in the Microsoft ecosystem.
5. Apache Cordova
- Overview: Apache Cordova enables developers to build mobile applications using HTML5, CSS3, and JavaScript.
- Key Features:
- Access to native device APIs via plugins.
- Supports a wide range of platforms, including Android and iOS.
- Large community with extensive plugin availability.
- Ideal For: Projects prioritizing rapid development and broad device compatibility.
6. Tauri

- Overview: Tauri is a lightweight framework for building cross-platform desktop and mobile applications using web technologies and Rust.
- Key Features:
- Smaller bundle sizes compared to Electron.
- Enhanced security features.
- Supports Windows, macOS, Linux, Android, and iOS.
- Ideal For: Developers seeking efficient and secure applications with minimal overhead.
7. Xamarin
- Overview: Xamarin allows developers to build native apps for multiple platforms using C#.
- Key Features:
- Shared codebase across platforms.
- Access to native APIs.
- Integration with Visual Studio.
- Ideal For: Developers familiar with the .NET ecosystem aiming for native performance.
8. Jetpack Compose (Android)

- Overview: Jetpack Compose is Google’s modern toolkit for building native Android UIs using Kotlin.
- Key Features:
- Declarative UI approach simplifies UI development.
- Seamless integration with existing Android codebases.
- Enhanced tooling support in Android Studio.
- Ideal For: Android developers seeking a modern and efficient UI development experience.
9. Kotlin Multiplatform Mobile (KMM)

- Overview: KMM enables sharing code between Android and iOS platforms using Kotlin.
- Key Features:
- Write business logic once and deploy on both platforms.
- Access to platform-specific APIs when needed.
- Strong support from JetBrains and the Kotlin community.
- Ideal For: Teams aiming to maximize code reuse while maintaining native UI experiences.
10. Unity

- Overview: Primarily known for game development, Unity also supports building interactive mobile applications.
- Key Features:
- Robust 2D and 3D rendering capabilities.
- Cross-platform deployment.
- Extensive asset store and community support.
- Ideal For: Developers creating visually rich, interactive applications or games.
⚔️ Flutter vs. React Native: 2025 Showdown
The debate between Flutter and React Native continues in 2025, with both frameworks offering compelling features.
Performance
- Flutter: Utilizes AOT compilation and the Impeller engine, delivering near-native performance and smooth animations.
- React Native: The introduction of the Fabric architecture and Hermes engine has significantly improved performance, though it may still lag in graphics-intensive applications.
Development Experience
- Flutter: Offers a rich set of customizable widgets and a structured architecture, though it requires learning Dart.
- React Native: Leverages JavaScript/TypeScript, making it accessible for web developers, with a vast ecosystem of libraries.
Community and Ecosystem
- Flutter: Rapidly growing community with strong support from Google.
- React Native: Established community with extensive third-party libraries and tools.
📈 Mobile SEO Trends in 2025
Staying updated with mobile SEO trends is crucial for app visibility and user engagement.

Simplified URL Structures
Google has removed breadcrumbs from mobile search results, displaying only the domain name to enhance clarity on smaller screens.
App Indexing
Ensuring your app content is indexable by search engines can improve discoverability. Implementing deep linking and structured data is essential.
Performance Optimization
Fast-loading, responsive apps provide better user experiences and are favored in search rankings. Leveraging tools like Google’s Lighthouse can help assess and improve performance.
🧠 Conclusion

Choosing the right cross-platform development tool in 2025 depends on your project’s specific needs, team expertise, and long-term goals. Flutter and React Native continue to lead the landscape, each with unique strengths. Emerging tools like Tauri and Kotlin Multiplatform Mobile offer exciting alternatives for developers seeking efficiency and flexibility. Staying informed about mobile SEO trends ensures your app remains visible and competitive in an ever-evolving digital landscape
Future-Proof Your Business with Incognitai
Stay ahead in today’s digital-first world with next-gen IT solutions and smart digital marketing strategies from Incognitai.
Unlock your brand’s potential with technology that drives growth, streamlines efficiency, and powers innovation for the future.
📧 Email: admin@incognitai.com
📞 Call: +91 99522 89956
Let’s engineer your IT success, today.

𝐓𝐨𝐩 𝟏𝟎 𝐂𝐲𝐛𝐞𝐫𝐬𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐓𝐡𝐫𝐞𝐚𝐭𝐬 𝐢𝐧 𝟐𝟎𝟐𝟓 𝐚𝐧𝐝 𝐇𝐨𝐰 𝐭𝐨 𝐌𝐢𝐭𝐢𝐠𝐚𝐭𝐞 𝐓𝐡𝐞𝐦?
Jun 04th, 2025
As we move deeper into 2025, cyber threats are becoming more intelligent, automated, and harder to detect. From AI-generated deepfakes to the threat of quantum computing, today’s digital dangers demand smarter defenses. Whether you’re a business owner, IT professional, or security enthusiast, staying ahead of these threats is no longer optional—it’s essential. Here’s your guide to the top cybersecurity threats in 2025 and how to defend against them.

𝟏. 𝐀𝐈-𝐏𝐨𝐰𝐞𝐫𝐞𝐝 𝐂𝐲𝐛𝐞𝐫𝐚𝐭𝐭𝐚𝐜𝐤𝐬: 𝐓𝐡𝐞 𝐃𝐨𝐮𝐛𝐥𝐞-𝐄𝐝𝐠𝐞𝐝 𝐒𝐰𝐨𝐫𝐝
AI is revolutionizing both offense and defense in cybersecurity. Hackers now use AI to create intelligent malware and hyper-personalized phishing schemes.

𝐇𝐨𝐰 𝐭𝐨 𝐌𝐢𝐭𝐢𝐠𝐚𝐭𝐞:
1.Implement AI-driven security systems.
2.Train staff to spot AI-manipulated scams.
3.Partner with AI researchers to anticipate threats.
𝟐. 𝐃𝐞𝐞𝐩𝐟𝐚𝐤𝐞 𝐒𝐜𝐚𝐦𝐬: 𝐓𝐡𝐞 𝐑𝐢𝐬𝐞 𝐨𝐟 𝐒𝐲𝐧𝐭𝐡𝐞𝐭𝐢𝐜 𝐃𝐞𝐜𝐞𝐩𝐭𝐢𝐨𝐧
Deepfakes are no longer experimental—they’re a real threat. They can be used to impersonate executives or create fake video calls that trick employees into sharing data or sending money.

𝐇𝐨𝐰 𝐭𝐨 𝐌𝐢𝐭𝐢𝐠𝐚𝐭𝐞:
1.Use video authentication tools.
2.Confirm sensitive requests through multiple channels.
3.Raise awareness about deepfake tactics.
𝟑. 𝐐𝐮𝐚𝐧𝐭𝐮𝐦 𝐂𝐨𝐦𝐩𝐮𝐭𝐢𝐧𝐠 𝐓𝐡𝐫𝐞𝐚𝐭𝐬: 𝐁𝐫𝐞𝐚𝐤𝐢𝐧𝐠 𝐄𝐧𝐜𝐫𝐲𝐩𝐭𝐢𝐨𝐧 𝐍𝐨𝐫𝐦𝐬
Quantum computing may still be emerging, but it poses a serious risk to traditional encryption methods, making long-term data vulnerable.

𝐇𝐨𝐰 𝐭𝐨 𝐌𝐢𝐭𝐢𝐠𝐚𝐭𝐞:
Begin migrating to quantum-safe encryption.
Review existing data protection protocols.
Stay informed on cryptographic developments.
𝟒. 𝐑𝐚𝐧𝐬𝐨𝐦𝐰𝐚𝐫𝐞-𝐚𝐬-𝐚-𝐒𝐞𝐫𝐯𝐢𝐜𝐞 (𝐑𝐚𝐚𝐒): 𝐂𝐫𝐢𝐦𝐞 𝐟𝐨𝐫 𝐇𝐢𝐫𝐞
Ransomware kits are now being sold on the dark web, allowing anyone to launch attacks. The result? A surge in ransomware incidents.

𝐇𝐨𝐰 𝐭𝐨 𝐌𝐢𝐭𝐢𝐠𝐚𝐭𝐞:
1.Maintain regular offline backups.
2.Segment your networks.
3.Train employees to avoid phishing and suspicious links.
𝟓. 𝐈𝐨𝐓 𝐕𝐮𝐥𝐧𝐞𝐫𝐚𝐛𝐢𝐥𝐢𝐭𝐢𝐞𝐬: 𝐔𝐧𝐩𝐫𝐨𝐭𝐞𝐜𝐭𝐞𝐝 𝐃𝐞𝐯𝐢𝐜𝐞𝐬 𝐄𝐯𝐞𝐫𝐲𝐰𝐡𝐞𝐫𝐞
Smart devices—from thermostats to factory equipment—can be exploited as entry points into networks if not secured properly.

𝐇𝐨𝐰 𝐭𝐨 𝐌𝐢𝐭𝐢𝐠𝐚𝐭𝐞:
1.Change default settings and passwords.
2.Keep firmware updated.
3.Monitor traffic from IoT devices.
- 𝐒𝐮𝐩𝐩𝐥𝐲 𝐂𝐡𝐚𝐢𝐧 𝐀𝐭𝐭𝐚𝐜𝐤𝐬: 𝐈𝐧𝐝𝐢𝐫𝐞𝐜𝐭 𝐄𝐧𝐭𝐫𝐲 𝐏𝐨𝐢𝐧𝐭𝐬
Attackers are no longer targeting companies directly—they’re breaching suppliers and vendors to access bigger targets.
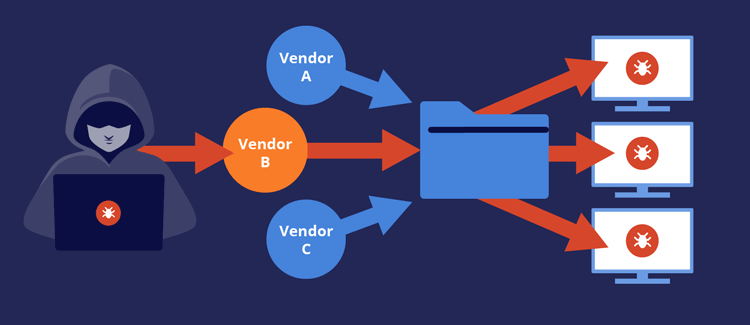
𝐇𝐨𝐰 𝐭𝐨 𝐌𝐢𝐭𝐢𝐠𝐚𝐭𝐞:
1.Audit third-party vendors regularly.
2.Use zero-trust architecture for external integrations.
3.Restrict access permissions by role.
𝟕. 𝐂𝐥𝐨𝐮𝐝 𝐒𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐌𝐢𝐬𝐜𝐨𝐧𝐟𝐢𝐠𝐮𝐫𝐚𝐭𝐢𝐨𝐧𝐬: 𝐓𝐡𝐞 𝐈𝐧𝐯𝐢𝐬𝐢𝐛𝐥𝐞 𝐑𝐢𝐬𝐤
Incorrect cloud settings have become a leading cause of data leaks. It’s not the cloud that’s unsafe—it’s how you configure it.

𝐇𝐨𝐰 𝐭𝐨 𝐌𝐢𝐭𝐢𝐠𝐚𝐭𝐞:
1.Use automated cloud security tools.
2.Regularly audit configurations.
3.Educate teams about cloud security best practices.
𝟖. 𝐈𝐧𝐬𝐢𝐝𝐞𝐫 𝐓𝐡𝐫𝐞𝐚𝐭𝐬: 𝐃𝐚𝐧𝐠𝐞𝐫 𝐟𝐫𝐨𝐦 𝐖𝐢𝐭𝐡𝐢𝐧
Employees or contractors—intentionally or not—can leak, steal, or destroy sensitive data, making insider threats an ongoing risk.

𝐇𝐨𝐰 𝐭𝐨 𝐌𝐢𝐭𝐢𝐠𝐚𝐭𝐞:
1.Monitor internal activities with behavioral analytics.
2.Enforce access control and segmentation.
3.Foster a culture of security responsibility.
𝟗. 𝐀𝐈 𝐢𝐧 𝐂𝐲𝐛𝐞𝐫 𝐃𝐞𝐟𝐞𝐧𝐬𝐞: 𝐒𝐦𝐚𝐫𝐭𝐞𝐫, 𝐅𝐚𝐬𝐭𝐞𝐫 𝐑𝐞𝐬𝐩𝐨𝐧𝐬𝐞
Just as AI can attack, it can defend. AI helps detect threats faster, analyze behaviors, and automate responses—cutting response times drastically.

𝐇𝐨𝐰 𝐭𝐨 𝐌𝐢𝐭𝐢𝐠𝐚𝐭𝐞:
1.Integrate AI-based detection tools.
2.Continuously train models with new threat data.
3.Combine AI with expert oversight.
𝟏𝟎. 𝐑𝐞𝐠𝐮𝐥𝐚𝐭𝐨𝐫𝐲 𝐏𝐫𝐞𝐬𝐬𝐮𝐫𝐞: 𝐂𝐨𝐦𝐩𝐥𝐢𝐚𝐧𝐜𝐞 𝐚𝐭 𝐭𝐡𝐞 𝐂𝐨𝐫𝐞
Regulations are evolving. Compliance is not just about avoiding fines—it’s about building trust and accountability in the digital age.

𝐇𝐨𝐰 𝐭𝐨 𝐌𝐢𝐭𝐢𝐠𝐚𝐭𝐞:
1.Assign a dedicated compliance lead.
2.Stay current on global and industry-specific regulations.
3.Use tools for automated policy enforcement and audit trails.
✅𝐓𝐚𝐤𝐞 𝐀𝐜𝐭𝐢𝐨𝐧 𝐍𝐨𝐰: 𝐏𝐫𝐨𝐭𝐞𝐜𝐭 𝐖𝐡𝐚𝐭 𝐌𝐚𝐭𝐭𝐞𝐫𝐬
Cybersecurity isn’t just an IT issue—it’s a business priority. Don’t wait until you’re the next headline. Whether you need a cybersecurity audit, employee training, or enterprise-grade protection, we’re here to help.
📧 Email: admin@incognitai.com
📞 Call: +91 99522 89956
𝐘𝐨𝐮𝐫 𝐝𝐞𝐟𝐞𝐧𝐬𝐞 𝐬𝐭𝐚𝐫𝐭𝐬 𝐧𝐨𝐰. 𝐋𝐞𝐭’𝐬 𝐦𝐚𝐤𝐞 𝐲𝐨𝐮𝐫 𝐝𝐢𝐠𝐢𝐭𝐚𝐥 𝐰𝐨𝐫𝐥𝐝 𝐦𝐨𝐫𝐞 𝐬𝐞𝐜𝐮𝐫𝐞!

𝐀𝐈 𝐯𝐬. 𝐇𝐮𝐦𝐚𝐧 𝐂𝐫𝐞𝐚𝐭𝐢𝐯𝐢𝐭𝐲: 𝐂𝐚𝐧 𝐆𝐏𝐓-𝟓 𝐑𝐞𝐩𝐥𝐚𝐜𝐞 𝐆𝐫𝐚𝐩𝐡𝐢𝐜 𝐃𝐞𝐬𝐢𝐠𝐧𝐞𝐫𝐬?
May 14th, 2025
In 2025, artificial intelligence (AI) has become an integral part of the creative industry, with tools like GPT-5 pushing the boundaries of what’s possible in graphic design. These advancements prompt a critical question: 𝐂𝐚𝐧 𝐀𝐈 𝐭𝐫𝐮𝐥𝐲 𝐫𝐞𝐩𝐥𝐚𝐜𝐞 𝐡𝐮𝐦𝐚𝐧 𝐠𝐫𝐚𝐩𝐡𝐢𝐜 𝐝𝐞𝐬𝐢𝐠𝐧𝐞𝐫𝐬?
𝐓𝐡𝐞 𝐄𝐦𝐞𝐫𝐠𝐞𝐧𝐜𝐞 𝐨𝐟 𝐀𝐈 𝐢𝐧 𝐆𝐫𝐚𝐩𝐡𝐢𝐜 𝐃𝐞𝐬𝐢𝐠𝐧:
AI-powered design tools have revolutionized the way creatives approach their work. Platforms such as Canva, Figma, and Adobe Firefly now incorporate AI features that automate tasks like layout generation, color palette suggestions, and image editing. For instance, Figma’s recent updates include AI-driven functionalities that allow designers to generate interaction code and create vector illustrations seamlessly.
These tools enhance efficiency, enabling designers to focus more on conceptual development rather than repetitive tasks. However, while AI can assist in the design process, it lacks the innate human ability to infuse emotion and context into visual narratives.
𝐆𝐏𝐓-𝟓: 𝐄𝐱𝐩𝐚𝐧𝐝𝐢𝐧𝐠 𝐭𝐡𝐞 𝐇𝐨𝐫𝐢𝐳𝐨𝐧𝐬 𝐨𝐟 𝐀𝐈 𝐂𝐫𝐞𝐚𝐭𝐢𝐯𝐢𝐭𝐲:
GPT-5, the latest iteration from OpenAI, showcases significant advancements in natural language processing and multimodal capabilities. Its ability to interpret and generate text, images, and even code positions it as a versatile tool in the creative sector.

Designers are leveraging GPT-5 to brainstorm ideas, generate content descriptions, and even draft initial design concepts. Despite these capabilities, GPT-5 operates based on patterns and data, lacking the subjective experiences and cultural insights that human designers bring to their work.
𝐓𝐡𝐞 𝐇𝐮𝐦𝐚𝐧 𝐄𝐥𝐞𝐦𝐞𝐧𝐭 𝐢𝐧 𝐃𝐞𝐬𝐢𝐠𝐧:
While AI tools offer speed and efficiency, the essence of impactful design lies in human creativity. Designers possess the ability to understand nuanced cultural contexts, evoke emotions, and tell compelling stories through visuals. These aspects are challenging for AI to replicate authentically.
Moreover, the design process often involves collaboration, feedback, and iterative refinement—areas where human intuition and interpersonal skills are paramount. AI can assist but not replace the dynamic interactions that drive innovative design solutions.
𝐓𝐡𝐞 𝐅𝐮𝐭𝐮𝐫𝐞: 𝐂𝐨𝐥𝐥𝐚𝐛𝐨𝐫𝐚𝐭𝐢𝐨𝐧 𝐁𝐞𝐭𝐰𝐞𝐞𝐧 𝐀𝐈 𝐚𝐧𝐝 𝐃𝐞𝐬𝐢𝐠𝐧𝐞𝐫𝐬:
The trajectory of AI in graphic design suggests a future of collaboration rather than replacement. Designers who embrace AI tools can enhance their workflow, allowing more time for creative exploration and strategic thinking. As noted by industry experts, the integration of AI into design education and practice is essential for staying competitive in the evolving landscape .

In conclusion, while GPT-5 and similar AI tools are transforming the graphic design industry, they serve as enhancements to human creativity, not substitutes. The unique human touch remains irreplaceable in crafting designs that resonate on a deeper, more personal level.
Future-Proof Your Business with Incognitai
Stay ahead in the digital-first world with next-gen IT solutions and smart digital marketing strategies from Incognitai.
Empower your brand with technology that drives growth, efficiency, and future-ready innovation.
📧 Email: admin@incognitai.com
📞 Call: +91 99522 89956
Let’s engineer your IT future, today.

Hello world!
Apr 18th, 2025
Welcome to WordPress. This is your first post. Edit or delete it, then start writing!